From Mainframe to Edge | Exploring Cisco Unified Edge Architecture and the Future of Intelligent Networks
In Episode 16 of the Tech Lounge podcast, we begin an architectural and historical journey together.
We start from the era of mainframes, move through cloud and fog computing, and then enter the world of edge computing—where processing, security, and decision-making are pushed to the edge of the network.
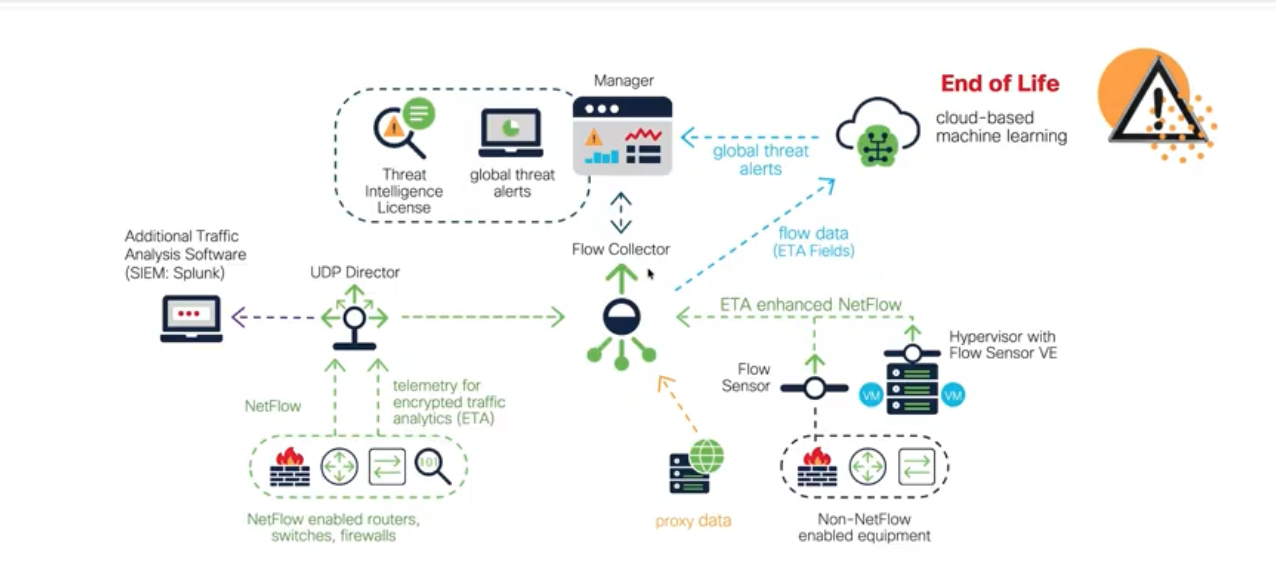
In this episode, we take an in-depth look at the Cisco Unified Edge architecture; a concept Cisco introduced this year as a unified vision for the edge. Its goal is to simplify, integrate, and intelligently orchestrate the network from the data center to the branch and the edge.
In this episode, you will learn:
- Why traditional architectures no longer meet today’s requirements
- What problem edge computing actually solves
- The real-world differences between cloud, fog, and edge
- How Cisco Unified Edge integrates networking, security, and compute at the edge
- How this architecture will impact the future of enterprise and industrial networks